
Streamlining the way IT professionals handle their cybersecurity, while preventing ransomware
The Platform that Prevents Ransomware
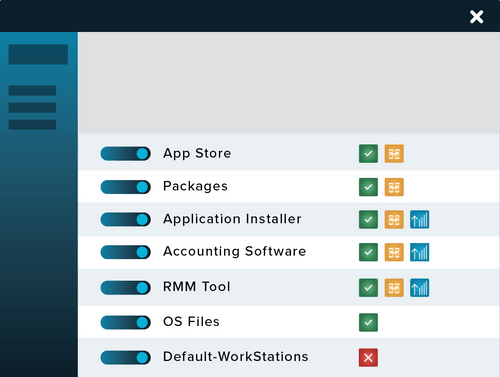
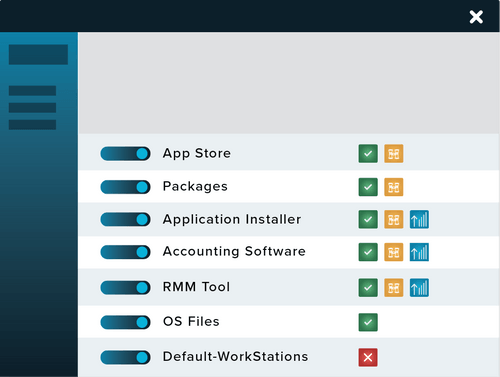
DAllow the software you need, and block everything else... Including ransomware.

Create a real-time inventory of your managed and unmanaged APIs. Uncover and remediate those that may be exposing sensitive data, not following specification definitions, or failing to use authentication best practices.
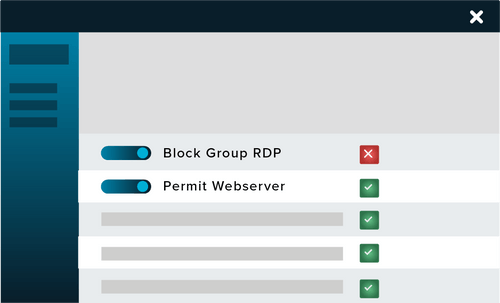
Network Control is an endpoint firewall solution that gives control over all network traffic, so you don’t leave devices or data vulnerable and exposed to cyber threats.

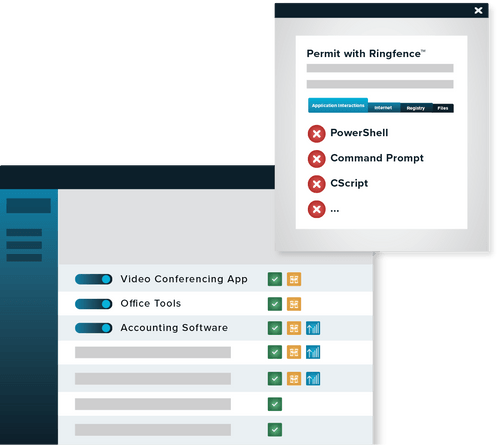
ThreatLocker Elevation Control provides an additional layer of security by allowing IT administrators to remove local admin privileges from their users while allowing them to run individual applications as an administrator.
Storage Control allows you to protect your data from unauthorized access or theft by setting granular policies over your storage devices.
Comprehensive threat detection and behavior monitoring so you can be proactive in the fight against cyber threats.
Learn how ThreatLocker can automatically create allowlist policies based on your organization's needs after deployment.


Learn how ThreatLocker Testing Environment helps administrators make quick and informed decisions on whether newly requested programs should be added to the allowlist.
ThreatLocker Configuration Manager enables IT professionals to set best practice configuration policies across their environment from a single central console.
Why ThreatLocker
Ransomware is malicious software that encrypts files, locking a victim out of their confidential data. If the victim pays the ransom, they may receive a decryption key that will restore their files and data access. If the demanded ransom is not paid, the threat actor may leak their data-on-data leak sites (DLS) such as the dark web and/or permanently block access to their files. As ransomware is distributed by cybercriminals, there is no guarantee that files will be decrypted if the ransom is paid, or that data wasn’t immediately leaked onto the dark web.
Application Allowlisting denies all executables, libraries, and scripts from executing, except those that are explicitly permitted to run in an environment.
Many cybercriminals use legitimate encryption tools such as 7-Zip to encrypt files. By using Allowlisting, legitimate tools that have not been explicitly allowed, including those that could be used to encrypt data, are blocked.
The process of deploying Allowlisting is extremely simple. ThreatLocker learns what is required in your environment and, once secured, blocks everything else.
PROACTIVELY PREVENTING THREATS